Hindsight is 20/20
The future of your blockchain is the extension of you, your values, and your security. Protect it from quantum threats before it’s too late.
The next generation of computers that use quantum mechanics to solve problems too complex for classical computers.
Why Are They a Concern For Blockchain Users
Who They Affect

Partners




The Problem
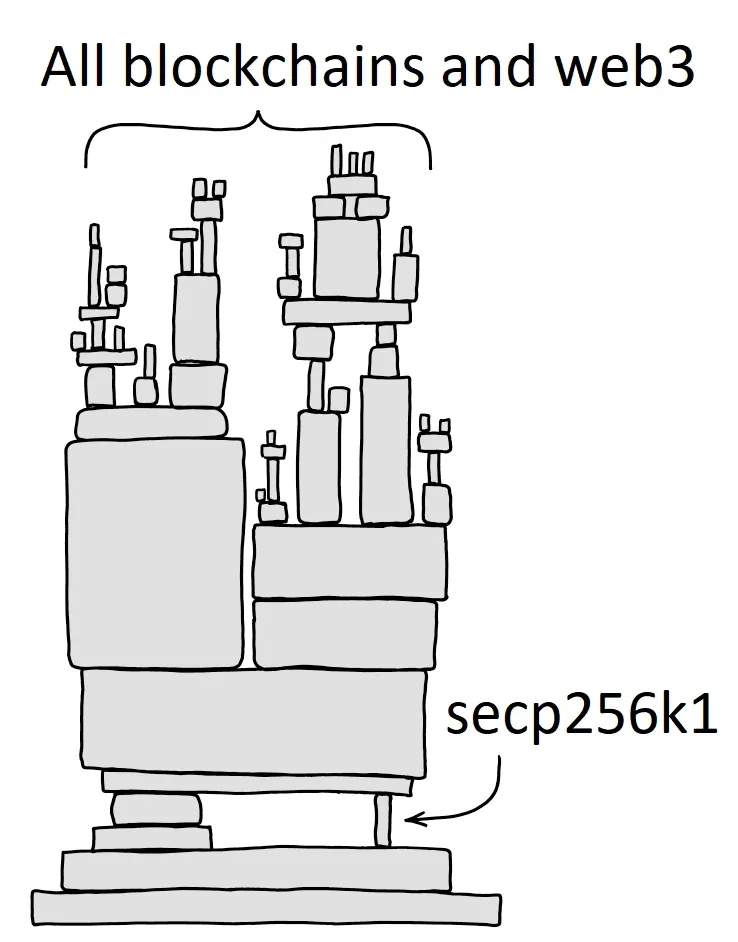
Eliptic curve cryptography is the Achille's heel of web3.
Sollicitudin massa maecenas purus adipiscing egestas natoque fringilla odio ac sodales
Sollicitudin massa maecenas purus adipiscing egestas natoque fringilla odio ac sodales
Sollicitudin massa maecenas purus adipiscing egestas natoque fringilla odio ac sodales
Sollicitudin massa maecenas purus adipiscing egestas natoque fringilla odio ac sodales
Sollicitudin massa maecenas purus adipiscing egestas natoque fringilla odio ac sodales
Sollicitudin massa maecenas purus adipiscing egestas natoque fringilla odio ac sodales
The Pauli Group Solution
With great power comes great responsibility.
Sollicitudin massa maecenas purus adipiscing egestas natoque fringilla odio ac sodales
Sollicitudin massa maecenas purus adipiscing egestas natoque fringilla odio ac sodales
Sollicitudin massa maecenas purus adipiscing egestas natoque fringilla odio ac sodales

The Problem
How To Secure Yourself Against Quantum Computers
Anchor uses the one-time signature scheme of Lamport signatures uses a random number generator and a cryptographically secure one-way hash function to arm your assets against quantum computers. We’ve added a requirement for a second stamp with stronger magic, this magic cannot be reversed by a quantum computer.
Community Buzz
What industry leading companies are saying
What IBM has to say
What Amazon has to say
Community Buzz
What industry leaders are saying
FAQ
Frequently Ask Questions
Lorem ipsum dolor sit amet, consectetur adipiscing elit.
Quantum computers will have the ability to recover the private keys from the public keys stored on blockchains. Almost all blockchains use elliptic curve cryptography for signing transactions on a ledger. While elliptic curve cryptography cannot be hacked with a classical computer, it is one of the easiest methods to break with a large enough quantum computer using Shor's discrete logarithm algorithm.
secp256k1 was almost never used before Bitcoin became popular, but it is now gaining in popularity due to its several nice properties. Most commonly-used curves have a random structure, but secp256k1 was constructed in a special non-random way which allows for especially efficient computation. As a result, it is often more than 30% faster than other curves if the implementation is sufficiently optimized. Also, unlike the popular NIST curves, secp256k1's constants were selected in a predictable way, which significantly reduces the possibility that the curve's creator inserted any sort of backdoor into the curve.







